User Tools
This is an old revision of the document!
Table of Contents
Keeping Your Computer Clean
In this day of evasive malware that can easily prevent your security applications from running and protecting you, it is even more important that you protect your computer from all of the nasty viruses, trojans, spyware, adware, rogues, etc. that are floating about on the Internet. This article will deal with several aspects of protecting your computer, including cleaning your computer up after getting infected.
1. Prevention
Understanding how to prevent infection is very important. This section has two subsections: a. Software Methods, b. User Methods. Software Methods is about the best applications that help prevent infection, and the best way to set up your computer to help prevent infection. User Methods deals with how to browse the Internet in a safe way, as well as describing some of the more common methods of social engineering and how you can avoid them.
a. Software Methods
It is important to have a good software setup. This includes good anti-virus and anti-malware applications running their real-time protection, but it also includes making sure that you have a secure web browser and that you keep your computer up to date.
I. Anti-Virus:
First we will concentrate on real-time security. This is things like your anti-virus that is protecting your computer. A lot of us have heard about Norton and McAfee, because they pay a lot of money to get manufacturers to install their software on new computers. The fact is that neither of these are good security applications, and they should never be used. Below is a list of anti-virus software that are far superior:
- AntiVir (free with ad, premium version available)
- NOD32 (costs $59.99 USD for 1 year)
- Kaspersky (stand-alone anti-virus costs $59.95 USD for 1 year)
II. Anti-Malware:
Having a good anti-virus is not enough. You will also need a good anti-malware or anti-spyware software with real-time protection. These types of applications will go above and beyond anti-virus software, concentrating on the types of things that anti-virus software is the most likely to miss. Here is a list of recommended software:
- Malwarebytes' Anti-Malware (real-time protection costs $24.95 USD for life)
III. HOSTS File:
Even with a good anti-malware/anti-spyware and a good anti-virus both running real-time protection, there is still more that can be done to block malicious content on the Internet. There is a file on every computer, called a HOSTS file, which can be used to silently block known malicious websites. Obviously it does not block unknown malicious websites, but it does add an extra layer of protection. Unfortunately playing around with the HOSTS file, and especially keeping it updated, is a little more than the average person would want to do. Fortunately there are security experts and programmers out there that made some nice free utilities that can do it for you. Here is a list of applications that be used to apply HOSTS files from either hpHosts or MVPS:
IV. Browsers:
On top of those layers of security, understand that there are other aspects of security that are important. Most of us are browsing around the Internet with a web browser that has the worst security record in the industry. Yes, I am talking about the Internet Explorer that came on your computer. The seemingly-harmless little blue 'e' that takes you to all of your favorite websites. So what could be better than the only web browser that Microsoft gave you when you first started up your computer? Here is a list of some popular alternatives that are far more secure:
- SRWare Iron (based on Google's Chrome, but doesn't invade your privacy)
- Google Chrome (same as SRWare Iron, except with mildly privacy-invading features)
- Flock (Firefox-based browser with social-networking features)
V. Updates:
It is very important to keep your software updated. Not just Windows, but also the various applications you use on a daily basis, such as; your web browser, your plugins and extensions for your web browser, your instant messaging clients, your e-mail client, your office suite, and of course any and all security software that you have.
Most of these applications have update notifications of some sort. For instance, OpenOffice.org will tell you that a new update is available, and ask you if you want to download it. Both Opera and Firefox will download and install updates automatically (with advanced settings to tweak how they do it). But when it comes to Microsoft applications, such as Microsoft Office (which contains Word, Excel, PowerPoint, Outlook, etc.) you need to take an extra step before you will automatically receive updates for them, even if you have Windows Update set to automatic. This extra step is called Microsoft Update, and it must be installed and activated to automatically receive updates to Microsoft products other than Windows itself.
In addition to making sure that you are getting all of the updates for all of the Microsoft applications that you use, you need to make sure that you are getting all of the updates for things like Java, Adobe Flash, and Adobe Reader. I cannot stress how important it is to keep these plugins up to date to help avoid infection.
If you are not sure what applications on your computer require updates, then here are a couple of resources that are invaluable:
VI. Autorun:
Autorun is that nifty little feature in Windows where, when you put a CD in the drive or plug a Flash drive into a USB port, Windows will look for a driver file that tells it what application to automatically run, and if none is found it gives you a list of options. At first such a feature seems like a great convenience, because now we never have to go looking through “My Computer” when we want to find the files on something we just plugged in.
Sadly, this convenience comes with a heavy price. When you plug a flash drive into an infected computer, many viruses/trojans/etc. will copy a couple of files to that flash drive. One of the files is a tiny application with a single purpose, which is to infect any computer that the flash drive is plugged into. The other file is a driver that tells Windows to load the malicious application when you plug in the flash drive.
So, what can you do to guard yourself from this? The best course of action is to disable autorun. Here are several tutorials on how to do this:
VII. Peer-2-Peer:
Peer-2-Peer (P2P) networking is a very common way to share files, and more than that it is the biggest way to pirate music and video on the Internet. Unfortunately, it is also one of the easiest ways for viruses and other malware to spread on the Internet. Many P2P applications (such as Limewire/Frostwire) will even automatically start sharing all of your private files without your knowledge, which means you lose all privacy on your own computer, and you could unknowingly become a participant in not only music and media piracy but software piracy as well. Worse than that is the fact that they usually install startup items on your computer, which means that whenever your computer is on it is sharing your files, and any files that you have downloaded through these P2P networks.
OK, so maybe you don't care that you are sharing your private files all of the time, or that some (if not all) of the content you are sharing is being shared illegally. Even if that is the case, you have to remember that there are other people using these filesharing networks who do not understand this. This sets up a case where viruses, like virut, can easily infect any executables or screensavers that a person is sharing, and often an anti-virus cannot tell that something malicious has been injected into a legitimate application or they are unable to repair the infected application without deleting it (otherwise file injectors like virut would not be an issue). When you take this into consideration, you have to assume that most applications and screensavers you download from P2P networks like Limewire are already infected.
Is there never a need for P2P filesharing? That depends on which network. When it comes to the networks used by things like Limewire, there are really no good reasons to be using them. When it comes to something like BitTorrent, then it's not as bad. For instance, most Linux distributions are available via BitTorrent. There are people who make free movies and distribute them via BitTorrent. There are Churches that distribute DVD-quality sermons through BitTorrent. The list of good uses is not endless, but it's much larger than some might think. The problem is that while you are using BitTorrent for good things, there could always be people sharing parts of the file who are sending you bad/corrupt data, or any number of other dastardly things. It is important to protect yourself from these things, and while the IP Blocking in Malwarebytes' Anti-Malware will block some of it, it does not go far enough for simple P2P protection. You need more than that:
- PeerBlock 2 (note that there could be issues with this and other IP Blocking techniques running at the same time)
b. User Methods
More important than security software is the knowledge that a user (that would be anyone using a computer, aka: you) has about threats on the Internet. In this section we will attempt to cover the most common ways that malicious software gets on your computer - aka: tricking you into thinking that it's something you want.
I. Download This Codec:
One of the most popular ways of tricking someone into believing that they want something malicious is to convince them that it is something they need to watch a video that they are interested in. Most people just assume that a video will play when you visit a site with a video, but what they don't realize is that when a video is loaded that two things are needed for it to play:
- The appropriate plugin for the web browser.
- A codec that describes how to decode and play the video.
Now, when you go to YouTube, and sites like it, the videos play through a plugin called Flash (which is currently made by Adobe). As long as you have the Flash plugin, which Microsoft distributes with Internet Explorer and keeps updated via Windows Update, then you are able to play videos on sites such as YouTube. When you are poking around on the Internet, sometimes you will come across videos that do not use Flash, but instead use other plugins. These normally play through Windows Media Player, but if Windows Media Player does not have the codec that describes that type of video, then you will receive an error. Some malicious websites will take advantage of the confusion surrounding codecs, and trick people into installing something malicious by showing them a webpage that looks like it has an interesting video on it, and then telling them that they need to download a codec for a video to play. This is the point at which you should close your web browser as fast as you can, and manually update all of your security software in order to run scans of your computer.
A good rule of thumb is to never click on a link to a video on some random website that you are not familiar with. Places like YouTube, DailyMotion, Google Video, Yahoo! Video, etc. are OK, but unless you are familiar with the site, or know people who use it without strange computer problems, then probably best to stay away from it.
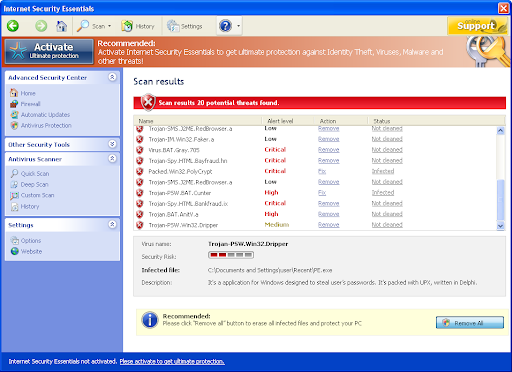
II. Your Computer Is Infected:
Every now and then, as your are browsing around the Internet, you will get a seemingly random popup that looks like an anti-virus scan telling you that your computer is infected and asking you to click to take some sort of action to remedy the situation. Many times the popup will not look anything like your anti-virus software, but will try to look like it is some sort of official Windows popup to trick you into thinking that it is legitimate. Many times they will even use official looking Microsoft graphics to make them look legitimate, such as the following screenshot (complements of the S!Ri.URZ Blog):
If you see something like this, then the best course of action is to close your Internet browser immediately, and run an anti-malware scan (make sure to update your anti-malware tool before running the scan). Many times these things will attempt to use security vulnerabilities in popular Internet browsers (especially Internet Explorer) to cause a trojan to run on your computer, which will install a rogue and a rootkit to prevent you from removing it. It can do this in a matter of seconds, however if you catch it quickly enough, then you may be able to remove the trojan before it installs a rootkit.
2. Removal
Prevention is bound to fail every now and then. No matter how safely you browse the Internet, and no matter how many levels of security you have, your computer can still get infected.
The most obvious reason for this is that, even the most educated person can still make a mistake. Even experts will sometimes accidentally click on a link that they shouldn't have.
The other main reason is because anti-virus software detects viruses and malware based on whether or not it's been seen before. If something new comes out, it often takes a few days (if not weeks) for the security industry to catch up. Yes, most security applications have what are called heuristics, which are supposed to detect new variants of viruses and such without the need for them to have been seen before, but even in an application with as good of heuristics as Malwarebytes' Anti-Malware the research team who maintains the database has to have come in contact with something before they can write heuristics that catch it.
a. Automated Removal
Automated removal tools are plentiful these days, and there are a lot of rogues out there that are posing as popular removal tools just to steal your money (Malware Removal BOT, AntiMalware Pro, and MalwareBot Malware Remover are just a few of many). It is important that you make sure the get legitimate tools from legitimate download sites.
Some good malware/spyware removal tools include the following:
- Spybot Search & Destroy (I highly recommend that you do not allow it to install its “TeaTimer” component)
Also, most anti-virus software vendors have special tools designed to remove viruses. They will often be offered as one tool to remove all variants of a single virus, and so if you have multiple viruses you may need to download multiple tools. Here is a list of links to some of these tools from some anti-virus vendors:
Sometimes rootkits can prevent removal of common infections, and rootkits such as TDSS, TDL3, and TDL4 can be very difficult to disable and remove without a Windows CD or some other way of repairing your computer's boot sector from a bootable CD or DVD. Kaspersky's TDSSKiller can often remove these rootkits on its own, however we highly recommend that you seek assistance from an expert in malware removal for instructions on how to proceed if you believe that your computer is infected with the TDSS, TDL3, or TDL4 rootkits as tools like Kaspersky's TDSSKiller can be dangerous if you run them without expert assistance/instructions.
b. Manual Removal
Since automated tools cannot possibly remove everything, there are various online security communities that have forums where trained experts will be able to assist you with manually removing infections from your computer. Here are a list of some of those forums:
Credits/Acknowledgments
Some of the content in this article was added or changed at the suggestions of the following contributors:
- Ron Lewis (Manager of Online Support - Malwarebytes Corporation)
- Samuel E Lindsey (Malwarebytes Quality Assurance)
- extremeboy (volunteer expert at Malwarebytes.org)
- Steven Burn (Malwarebytes Researcher, hpHosts maintainer, etc)